You’ve seen the memes. Maybe you’ve even clicked one. One second you’re looking at a blurry photo of a cat, and the next, some random person on Discord is reciting your home city and ISP. It’s a classic internet prank—or a serious privacy concern, depending on which side of the screen you’re on. People always ask how to hide Grabify link in image files because they want that seamless, "invisible" click. But honestly? Most of the tutorials you find online are either outdated or flat-out dangerous for your own digital hygiene.
The reality of IP logging has changed. In 2026, browsers are smarter, and social media platforms are basically giant filters that strip out metadata before it ever reaches the end user. If you're trying to figure out how to hide Grabify link in image embeds, you have to understand the cat-and-mouse game between tracking services and modern security headers. It isn't just about making a link look like a JPG. It's about how the browser handles a redirect when it expects an image.
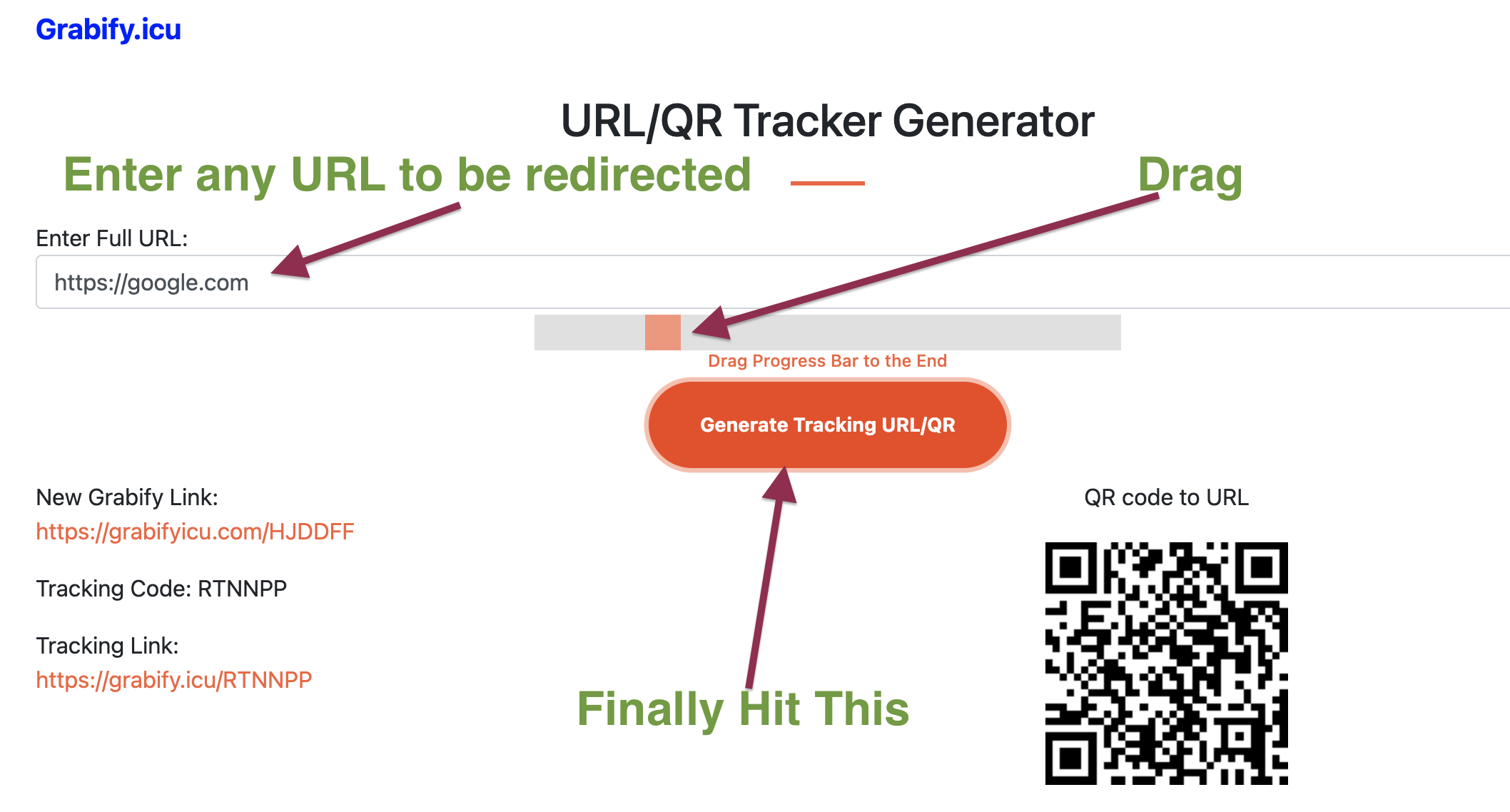
Why Hiding Grabify Links Isn't Just "Renaming a File"
Let’s get one thing straight: you can't just change .html to .jpg in a URL and expect it to work. That’s not how the internet's "handshake" functions. When a browser sees a link, it asks the server, "Hey, what is this?" The server responds with a MIME type. If you’re trying to hide Grabify link in image headers, the server has to trick the browser into thinking it’s looking at a visual asset while the backend logs the IP address.
Most people fail because they use the "Link Shortener" feature on Grabify and stop there. That's amateur hour. Services like Bitly or Cuttly are flagged instantly by Discord, Slack, and even Gmail. If you want to hide Grabify link in image displays effectively, you need to leverage the "Image Logger" feature specifically, which generates a transparent 1x1 pixel or a custom-uploaded image. But even then, there’s a catch.
Most platforms now use "Image Proxies." When you post a link on Twitter or Discord, their servers—not the user's phone—go and fetch the image. So, if you check your Grabify logs, you might just see an IP address belonging to a Google or Amazon data center. You didn't get the user; you got the bot.
👉 See also: Why Everyone Is Obsessed With the Rose Gold Keyboard Case Right Now
The Technical Reality of Transparent Pixels
So, how do the pros actually do it? It’s usually through a method called a "tracking pixel." It’s a tiny, invisible image.
- Select a real image host: Don't just use the default Grabify domain. Everyone knows
grabify.link. Use their "Link Expansion" or "Custom Domain" features to pick something that sounds boring, likeimages-cache.comorstorage-cdn.net. - The Redirect Trap: You aren't just sending them to a link; you're embedding the link inside an image tag. In HTML, this looks like
<img src="your-grabify-link-here">. - File Extensions: Grabify allows you to add an extension to your link. Use it. Adding
.jpgor.pngto the end of your tracking code makes it look legitimate to both the user and certain basic filters.
But here is the kicker. If you're trying to hide Grabify link in image previews on a site like Facebook, it’s nearly impossible now. Why? Because Facebook’s "Safe Browsing" crawler will visit the link first. It sees the redirect. It flags it as "suspicious" or simply refuses to generate the preview.
The Ethics and the "No-Go" Zones
We have to talk about the "why" here. Security researchers use these tools to find out if someone is accessing a server they shouldn't be. It's a "canary in a coal mine" tactic. On the flip side, people use it for harassment. Don't be that person. Understanding how to hide Grabify link in image assets is a lesson in how the web works, but using it to doxx someone is a one-way ticket to getting banned—or worse, legal trouble.
📖 Related: Why those final pictures from Cassini still haunt us years later
Also, be aware that many VPNs and browsers like Brave or Safari now have "Link Protection." They will strip the tracking parameters or use a relay to hide the user's real IP. So even if you're successful in hiding the link, the data you get back might be totally useless. It’s a game of diminishing returns.
Advanced Obfuscation: Moving Beyond the Basics
If you really want to hide Grabify link in image embeds for a legitimate reason—like tracking if your proprietary artwork is being stolen and viewed—you should look into "Meta Tag" redirects. Instead of a direct link, you point the user to a page that looks like a dead end but triggers the logger in the background.
Most users expect a certain behavior when they click an image. They expect it to get bigger. If they click a "photo" and it opens a browser tab that stays white for three seconds before showing the image, they know something is up. The key to successfully hiding the trace is speed. Using a fast DNS and a custom domain with a low TTL (Time To Live) makes the redirect happen so fast the human eye barely catches the URL change in the address bar.
👉 See also: The Lightning Strike Legend: When Was Nikola Tesla Born and Why It Matters
Common Mistakes That Give You Away
- Using the "Grabify" name: Seriously, it’s the biggest giveaway.
- Forgetting HTTPS: If your link is
httpand the site ishttps, the browser will throw a big "Not Secure" warning. It kills the illusion instantly. - Bad File Names: Don't name your link
track-you.jpg. Name it something likeDCIM_00421.jpg. Authenticity is in the boring details.
How to Protect Yourself From These Links
Since we’re talking about how to hide Grabify link in image files, we should probably talk about how to spot them. It's only fair. Information wants to be free, right?
First, hover over everything. If the URL at the bottom of your browser doesn't match where you think you're going, don't click. Second, use a "Link Unshortener" service. There are sites where you can paste a suspicious link, and it will tell you exactly where that link goes without you having to actually visit it.
Actionable Next Steps for Digital Privacy
If you're worried about people using these tactics on you, or if you're experimenting with these tools for research, here’s what you should do right now:
- Use a VPN: This is the simplest way to make IP loggers irrelevant. If they log you, they get the IP of a server in Switzerland or New York, not your house.
- Disable Auto-Load Images: In your email client (like Outlook or Gmail), turn off the setting that automatically displays images. This prevents tracking pixels from "firing" the moment you open an email.
- Check for Redirects: Use browser extensions like "Redirect Path" to see every jump a URL makes. If you see a Grabify domain in the chain, you know you've been tagged.
- Custom Domains for Creators: If you are a creator trying to protect your work, skip Grabify and use a professional service like Pixsy or your own self-hosted tracking script. It looks more professional and is less likely to be flagged as malware.
Understanding the mechanics of how to hide Grabify link in image files is basically a crash course in how the modern web handles data. It's about MIME types, server-side requests, and the constant battle for privacy. Whether you're a curious student or a security pro, remember that the "stealth" of a link is only as good as the domain it's hosted on. Stick to custom solutions if you want results, and always use a VPN if you want to stay off someone else's log.